If you have an Android device, you are probably well aware of the Stagefright bug.
Google, Samsung, HTC, LG, Sony and Blackphone handsets as well as the different carriers released a patch for Stagefright, but apparently it may not be enough.
Security firm Exodus Intelligence uncovered a mistake in a particular source-code tweak, which was responsible for crashing a device when data in a multimedia message was being opened. And, according to the company, it could be exploited.
For its part Exodus said:
“There has been an inordinate amount of attention drawn to the bug — we believe we are likely not the only ones to have noticed it is flawed. Others may have malicious intentions,”
A malformed MP4 video file crashes even in patched Android Stagefright libraries, leaving devices on which they’re running vulnerable to attack.
This particular problem was discovered around July 31, when Exodus Intelligence security researcher Jordan Gruskovnjak noticed a severe problem with the proposed patch. He crafted an MP4 to bypass the patch and was greeted with a crash when it was tested.
It is important to note all Common Vulnerabilities and Exposures (CVEs) were patched, and Google has assigned the Exodus discovery with CVE-2015-3864, so it is well aware of the problem.
Contents
So What is Stagefright and Why is It So Dangerous?
According to Zimperium:
“These vulnerabilities are extremely dangerous because they do not require that the victim take any action to be exploited. Unlike spear-phishing, where the victim needs to open a PDF file or a link sent by the attacker, this vulnerability can be triggered while you sleep.” The company went on to say, “Before you wake up, the attacker will remove any signs of the device being compromised and you will continue your day as usual — with a trojaned phone.”
The Android Stagefright exploit is able to use flaws in the Android OS that it uses to process, play, and record multimedia files.
By sending an MMS, Stagefright can get into your device and, once it is infected, the attacker gains remote access to your microphone, camera, and external storage. In some instances, root access to the device can also be gotten.
The Android Stagefright bug was originally discovered by Zimperium zLabs VP of Platform Research and Exploitation Joshua J. Drake, in April. He later said he and his team believe it to be “the worst Android vulnerabilities discovered to date,” and that, “It critically exposes 95 percent of Android devices, an estimated 950 million devices.”
Zimperium reported the vulnerability to Google along with patches, and it acted quickly by applying the patches to internal code branches within 48 hours.
What Can You Do Until There is a Definitive Fix to the Problem?
First of all, only respond to messages from sources you trust. Additionally, disable the auto-download feature for MMS on SMS, Hangouts and videos on apps you have installed on your device.
Each app and device has its own location, but it is generally under settings and media download. If you can’t find it for your particular application, contact the app publisher.
Earlier this month, Google announced it will be issuing monthly security patches for Android devices at the Black Hat security conference, with Samsung following suit.
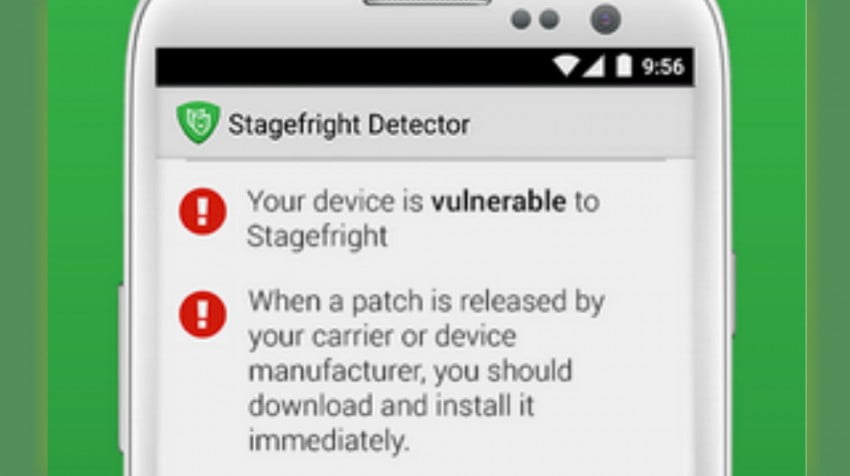
The company that first discovered the Stagefright has an app available on Google Play . It lets you know if your device is vulnerable, which CVEs your device is vulnerable to and whether you need to update your mobile operating system. It also tests for CVE-2015-3864, the vulnerability Exodus Intelligence identified.
Android is the most popular mobile OS platform, but it is very fragmented. This means not everyone is running the latest OS or security update, which makes it very difficult to ensure every Android device is protected.
If the manufacturer of your smartphone hasn’t patched your device, take matters into your own hands and make sure you have the latest update for your device at all times.
Image: Stagefright Detector/Lookout Mobile Security
[“source-smallbiztrends”]