Hemanth Joseph, a Kerala-based security researcher, has identified a bug running in iOS 10.1 version of Apple’s operating system that allowed him to bypass the Activation Lock on an iPad.
The Activation Lock in Apple’s iPhone or iPad is hard for someone other than owner of the device to hack and set it up as a new device.
Joseph claims to have bypassed the Activation Lock in a locked iPad by discovering a weakness in the device setup process running iOS 10.1, Forbes reported on Friday.
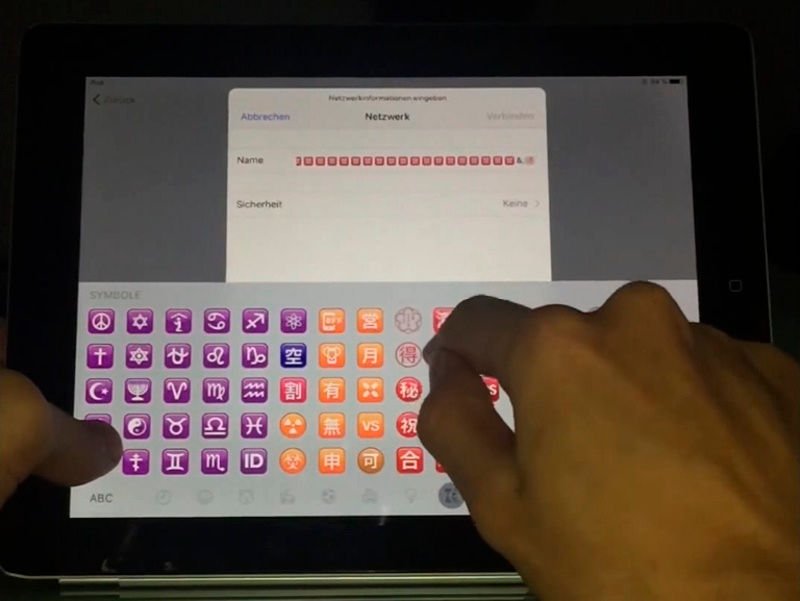
When Joseph was asked to select a Wi-Fi network, he chose ‘other network’ and selected WPA2-enterprise as the type of network to connect to, that gave him three input fields to fill – name, username and password.
Upon testing, he came to know that there is no character restriction in those fields and he typed thousands of characters, expecting that it would cause the software to crash.
This caused the iPad to freeze and then he locked it by closing Apple’s magnetic Smart Cover over the screen. After opening the cover, the device was at the same screen, but as few seconds passed by, it crashed to iOS home screen.
With this method Joseph claimed to have bypassed the Activation Lock and to have full access to the iPad. He communicated his findings to Apple, and his blog has screenshots of email correspondence with the company as well. The bug discovered by Joseph was reportedly fixed in an iOS update in October, with the release of iOS 10.1.1.
According to Joseph’s website, he is currently working as information security researcher at the firm Slash Secure and also serving as commander at Kerala Police Cyberdome. He also says he is founder of India’s first open security community for students called 0SecCon (www.0SecCon.com).
Joseph has also been listed Google’s Hall of Fame and received a bounty of $7,500 for reporting a critical vulnerability in Google Cloud Platform.
Separately, researchers at US-based Vulnerability Lab discovered a similar Activation Lock bug in iOS 10.1.1, one that is claimed to also work with the iPhone. Like Joseph, the team began by overloading the Wi-Fi setup fields and employed a smart cover. Just like in Joseph’s iPad scenario, the home screen appeared for an instant and then it’s gone.
Benjamin Kunz Mejri from the Vulnerability Lab says the team was able to recreate Joseph’s exploit even in iOS 10.1.1 by using iOS screen rotation and Night Shift mode. While the above video shows home screen access for a very short while, Mejri adds that this duration can be extended by quickly pressing the home button.
[“source-ndtv”]